0ld is g0ld
- Author
-
0x42697262
- Category
-
Misc
- Difficulty
-
Easy
- Play Date
-
2025/06/15 - 2025/06/15
Details
There is only 1 file in this challenge.
$ ls -la -rw-r--r-- 1 chicken chicken 197946 Sep 13 2017 '0ld is g0ld.pdf'
What to expect?
-
A password protected PDF
-
Press F to pay respect
|
Download the challenge here: 0ld_is_g0ld.zip Make sure the SHA-256 hash matches the original in the HackTheBox challenge website. |
Solution
I always tend to check the file type with file command even though it is not necessary here.
$ file 0ld_is_g0ld.zip 0ld is g0ld.pdf: PDF document, version 1.6, 1 page(s) (zip deflate encoded)
It’s a PDF file and there’s a "zip" word in it… could it be an archive?
I’ll try using strings.
Gathering for possible string passwords
Okay, nevermind that. It’s mostly gibberish.
What about exiftool?
$ exiftool '0ld is g0ld.pdf' ExifTool Version Number : 13.30 File Name : 0ld is g0ld.pdf Directory : . File Size : 198 kB File Modification Date/Time : 2017:09:13 02:18:32+00:00 File Access Date/Time : 2025:06:15 14:43:31+00:00 File Inode Change Date/Time : 2025:06:15 14:42:49+00:00 File Permissions : -rw-r--r-- File Type : PDF File Type Extension : pdf MIME Type : application/pdf PDF Version : 1.6 Linearized : No Encryption : Standard V4.4 (128-bit) User Access : Print, Modify, Copy, Fill forms, Extract, Print high-res Warning : Document is password protected (use Password option)
Nothing. Seems like I need to bruteforce the password.
Cracking the password
I tried binwalk but I didn’t see any binary.
I need a tool to bruteforce this PDF. Some quick search online gave me pdfrip.
Quite time consuming to compile in Rust though.
Alright, I was able to make it work.
$ pdfrip -n 12 -f '0ld is g0ld.pdf' wordlist ~/rockyou.txt
But this takes so much time.
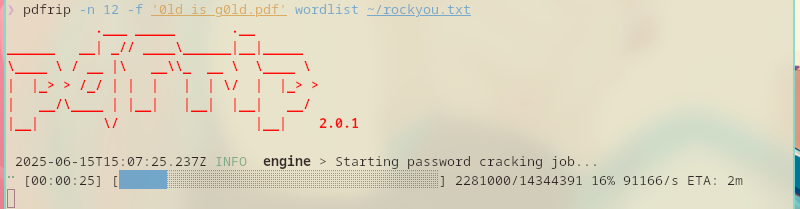
So, I moved to using pdf2john and john.
$ pdf2john '0ld is g0ld.pdf' > pdf.hash
$ john pdf.hash --wordlist=~/rockyou.txt
$ john --show pdf.hash
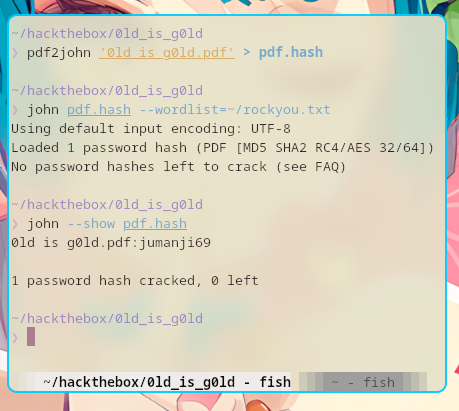
Ah, the password is jumanji69.
Finding the Flag
Time to open the PDF document.

I do not know this guy. Also where is the flag?
Ah, it’s at the very bottom of the document.
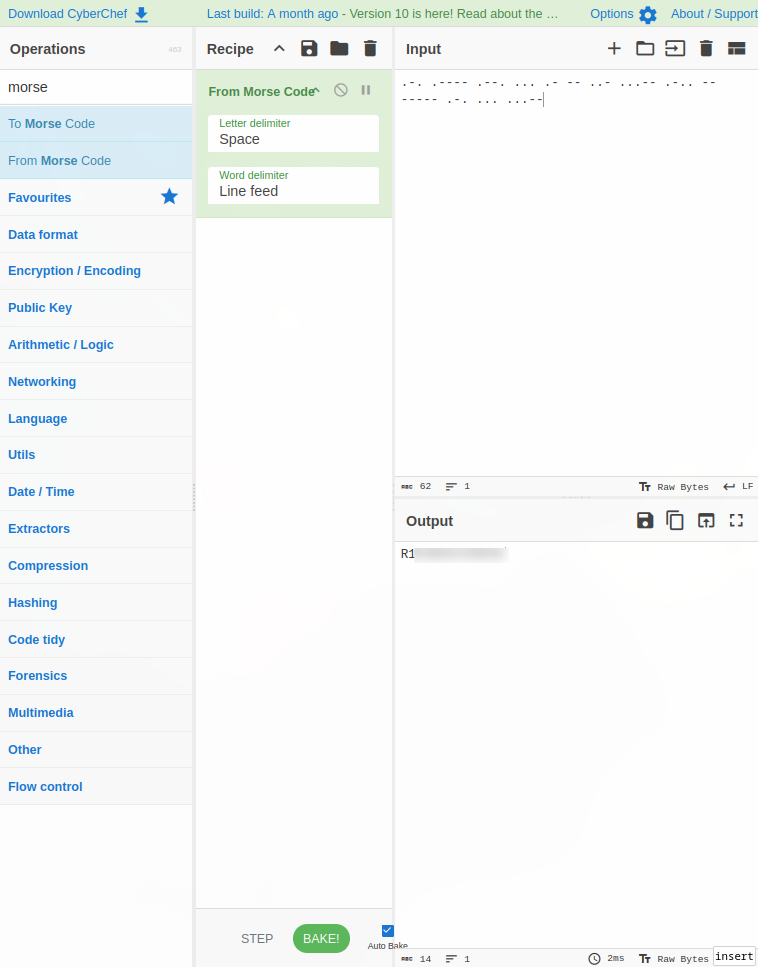
.-. .---- .--. ... .- -- ..- ...-- .-.. -- ----- .-. ... ...--
Converting this to plaintext from morse code gave me the flag.
Challenge solved.